 Last 12 months I was working on an interesting device that provides the network security features many companies and families are dreaming about. You probably already have heard about different threats out there like internet predators, viruses, spyware, dangerous websites, confidential information leaking from your business and others. Also you probably tried to find answers to questions like
Last 12 months I was working on an interesting device that provides the network security features many companies and families are dreaming about. You probably already have heard about different threats out there like internet predators, viruses, spyware, dangerous websites, confidential information leaking from your business and others. Also you probably tried to find answers to questions like
- Is my office network used appropriately? Do people really use it for work and not something else?
- Are my kids safe in the Internet? Are their virtual friends really friends?
- Why is my internet so slow?
- Who in my network is using the internet most, when and what for?
- How can I prevent my children or employees from browsing inappropriate content, wasting time in chats or games?
Finally, you might want to get answers to the questions immediately and you don’t want to spend a lot of time configuring every single computer in your network, installing software and other techi stuff … So the answer to all those questions is one small box called MineStream Defender and here is what it can do …
Well, let’s begin the overview of this product from the very beginning
Installation
Even installation process makes Defender different from most other networking devices. Installation of the box is not more difficult then installing a VCR or DVD player. In fact it is even easier as you need to plug just three cords. Here are the five simple steps to install the device in a small business network:
- Among your network devices find the one called router. How do you find it? In 90% of the cases it is written on the device with large white letters that it is the router. In 10% of the cases the letters are small and gray.
- Unplug the cable that is connected to router’s socket marked as LAN and connect it to socket marked as LAN on the Defender.
- Use included cable to connect socket marked as WAN on the Defender to the socket marked as LAN on the router. Basically you need to break the network line between your router and all the computers you’re going to monitor and control and plug Defender in between.
- Use included power adapter to connect the Defender to the power.
- Press power button on Defender
- Someone have connected an unauthorized internet-enabled equipment to your network, like a personal laptop or a handheld computer. The unauthorized equipment here is the equipment you, the rightful owner of your home or office network, have no idea about.
- You might have a security breach like unsecured wireless access point and someone you have no idea about is using your internet connection
- Your network might be hacked by someone
- Some of your home or office appliances might be internet-enabled even if didn’t know that. For instance you may forget that your Wii game console that has no network wires connected to it is still connected to the internet, so Defender can see it, record its activity and prevent it from working if necessary (see below)
- A friend of yours just came for a second, he has a smartphone or iPhone in his pocket and it automatically connected to your network for some reason (real case!)
- What sort of content should be considered inappropriate for the group (select from 70+ categories)
- When the group of computers is allowed to chat, browse web, play online games or have internet access at all. And yes, you can control game consoles like Wii, PlayStation or XBox from these menus as well.
- This menu has enough flexibility to configure some sites or even words to be included or excluded from the block list according or your personal preferences
- How do I know what computers access the Internet most?
- Statistics->Traffic, scroll down to the Hosts part of the page. The pie chart will answer your question
- What were the busiest hours in my network last month?
- Go to Statistics->Traffic, in the date selector choose Last 30 days, scroll to hourly part of the page.
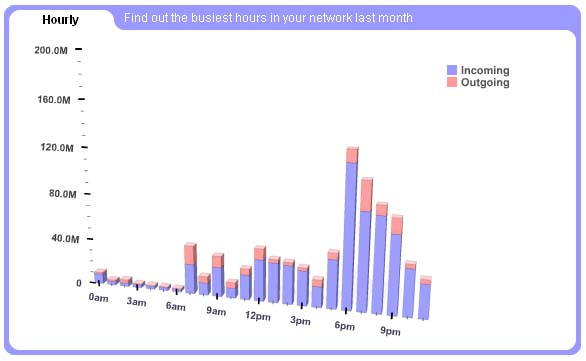
- What my traffic is spent for?
- Go to Statistics->Protocols page. It lists the most popular protocols in your network. For instance if the largest slice of the pie chart is HTTP(WEB) that means that the most traffic was spent for web browsing.
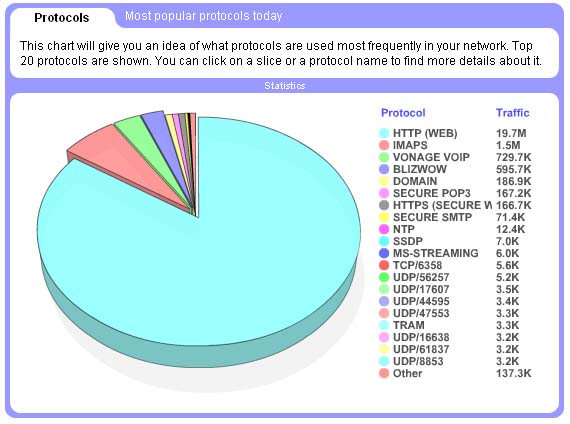
- Ok, now I know that most of the traffic in my network is web traffic. How can I find out who is consuming it? When people are browsing and what servers are they accessing?
- Naturally you can just click on the slice. this will bring up new window that will contain the answers to the questions stated above.
- The largest slice in protocols pie chart is “Other”. What is behind that “other”?
- “Other” are all protocols that are not in the top 20 list. To send out what are they just click on the slice and you’ll get the pie chart of the the most popular protocols ##20-40. What!? there is another “Other” slice? Well, you can click it too and go deeper. Once you find something interesting you can click on it and drill down for details.
- What are the most popular web servers in my network?
- Statistics->Servers answers this question. You don’t like reallybadsite.com being the largest slice? You always can go to block->Web and in the Blacklists->Websites enter this website: “reallybadsite.com”. Promise – it won’t be in top list anymore. And yes, you can click on slices to get more info. And the “Other” thing works here too, jut like for protocols.
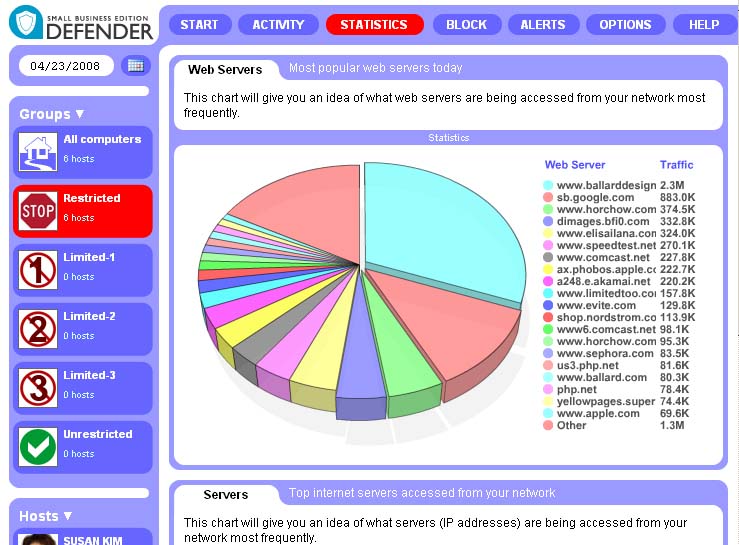
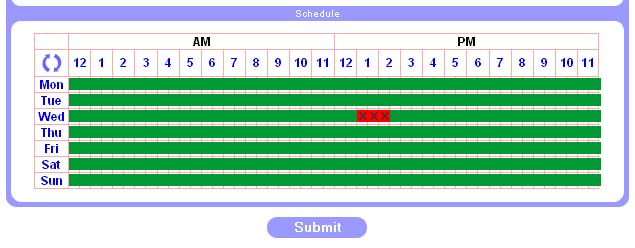
- I don’t like my kids playing online games on Wednesday between 1pm and 2:30pm!
- Go to Block->Online Games and select three cells when Wednesday row intersects with time between 1pm and 2:30pm. Hit “Submit”
- I’m trying to understand if my children have seen any inappropriate picture in the internet…
- Go to Activity->Images. Now you see all the pictures that had been seen in your network.

- … but I want to see this statistics only for a few computers for now, not for the entire network …
- For 90% of statistics you can select either group or individual host for which you want to see data for.
- My company is really HUGE. How can Defender monitor it?
- Sorry, Defender can’t. But our product called Citadel can. The concept of Citadel is a distributed network of devices similar to Defender that collect information from all your offices tha can be thousands of miles apart and aggregate this information. This information can further be viewed our tool called StreamView. See StreamView presentation here.
- I really don’t know what else I would like Defender to do …
- Good! But when you find out please let me know. We’re already considering versions that make coffee and establish security perimeter around your home.
In a minute Defender will start monitoring, controlling and recording traffic for all computers in your network. You don’t need to install anything on them. You don’t need to reconfigure your network. In fact you don’t need to ask your system administrator to install Defender in your network. You can ask your secretary to do that when she has a free minute.
In the beginning
So all your network traffic like websites content, images, emails, chats, searches, statistics and phone calls are now being recorded by Defender. That’s right, most phones in the offices this days operate via internet, so Defender can record them too! But all this recorded information is fo no use unless you can quickly analyze it, understand the threats at a glance and easily get details about every minute your network users spent in the internet. All this functionality is accessible via a web interface. You don’t need to install anything even to see the information. And forget about those totally confusing web interfaces you were probably struggling with when you were trying to install your home network. Defender’s interface is not for IT professionals like your system administrator or your child. It is for regular people, like parents, large business managers and small business owners.
 To access the device you just go to http://mydefender.minestream.com/ and login.
To access the device you just go to http://mydefender.minestream.com/ and login.
The default login is “admin” and the password is “admin” too. And if you’re too busy to change it after first login your Defender will be quite annoying reminding you to do it asap. IT IS REALLY IMPORTANT TO CHANGE YOUR INITIAL PASSWORD. This is true not only about Defender but also about any other network device.
So the very first thing that is not mandatory but highly recommended is going to Options->Settings and changing the login and password to something only you know. Also make sure that you recorded the login and the password somewhere else, because the system doesn’t provide the way to restore the login and password without loosing all the data collected. This is a bit inconvenient, but it is the only reliable way to prevent access to your valuable information by hacking the password.You can also adjust other settings on this page if you want to.
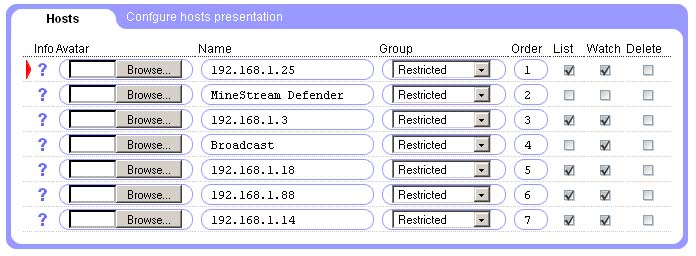
If you select Activity or Statistics you will probably find that almost all your network devices automagically appeared in the list of hosts at the left side of the screen. This is because Defender constantly discovers hosts in your network (a "host" here is any internet-enabled device, like PC, Mac, XBox, Wii, iPhone, PDA, internet-enabled coffeemaker etc).
Unfortunately the names of the hosts are really cryptic to non-techies. The numbers you see are the network addresses of all computers in your network prepended by the question mark. If you want something more user-friendly you can go to Options->Hosts and provide your own labels for each host in your office. You also can associate an avatar (small picture) with each device. This avatar will look way cooler then this blueish question mark.
The interesting question is how do you know who is who in the list of network hosts? You can get the answer if you click on the small question mark sign. This will bring up the window that will let you know the last web sites accessed from this host, last voice calls made and other information. If you’re still confused just go to http://mydefender.minestream.com from every computer in your network and notice the red triangle pointing to a line. This line references to the host you’re visiting Defender from. WARNING! Beware of keyloggers. Some computers may have special programs running that record all keystrokes. This means your password will be known to the person that installed the keylogger. So make sure you changed the password after you’re done with the hosts identification.
What if you still see some hosts you can’t identify? There are few possible cases:
Actually reading this paragraph is typically taking more time then finding what computer is what in the list. But if you’re a really busy boss you can click on the question mark next to the computer, write down the line named “Mac Address” and ask your system administrator to find out what piece of hardware in your office has this address. He is the techi guy, he knows the stuff. Also he will start thinking that you’re really smart if you know what “Mac address” is.
Well, now your Defender is not only collection information, but also shows you pictures of all your employees. By clicking on the picture you can find out favorite sports sites of this employee and how much time he or she is spending watching online video.
Now it is the time to tell Defender who is allowed to do what. If you have 30 computers in your network if would be pretty boring to set the same parameters for dozens of hosts. Instead you can arrange the hosts between different groups and then define settings for every group. Go to Options->Hosts again and select the group for each host. You can also exclude some hosts from being monitored or shown in the list of hosts at all. For instance you may not want your CFO’s computer activity to be recorded and probably the same is true for your personal computers. Now you can go through various submenus in Block main menu and for each group define such things as:
Would you like also to receive emails on inappropriate content access? Please go to Alerts->Configuration page and provide the email address you want to receive the alerts on. Oh, if you run a quick web search you’ll also find tons of online services that can forward emails to cellphones, so you can actually receive alerts on your cellphone too.
Did I say that all the options you just set are really optional? Yes, I did? Well, you do not have to configure them, everything works as is right after plugging the Defender to your network. At the same time Defender provides you many ways to customize it so you will get better result from it.
Let’s get more from it and get it quickly
So you have one minute to understand what’s up in your network. Click on Activity main menu item. This will bring up Activity summary page that will take only 20 seconds of your attention and will tell you if everything is ok with your network.
The 3-section green-yellow-red scale at the top-left shows you what’s up. If you’re in green zone – you have absolutely incredible children that have no idea how much illegal stuff they can find in the internet and not even trying to find it. It also means your employees are working hard for you all day long without even thinking about the score in Yanks vs Sox. Well being realistic your entire office is on that game and not working at all, that’s why you’re in the green zone. In most cases, however, your indicator will look like this:
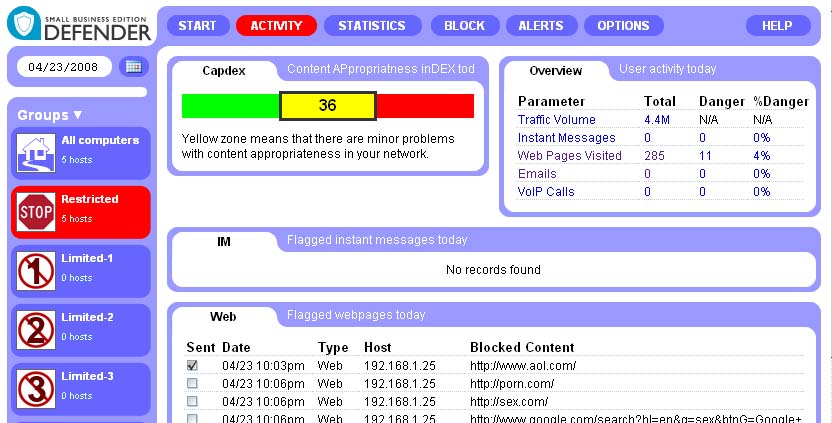
Below the scale, you will find the detailed description of why Defender thinks that not everything is so fine, what inappropriate websites were visited, wrong calls made and emails with your confidential information sent out.
Finally, red zone probably requires your immediate attention as most of the time your internet connection is spent for something completely inappropriate. This case most probably will take you more then 20 seconds and might ed up with a long meeting.
So, this page is very simple and very powerful. It is as easy as a traffic light but it at the same time it provides you with all details your need to understand what’s wrong in your network.
Let’s get even more – now you have some time for that
Ok, let’s answer more interesting questions:
![Stop Paying for SSL Certificates! Stop Paying for SSL Certificates! [Photo by Jason Dent on Unsplash]](https://andrey.mikhalchuk.com/wp-content/andrey.mikhalchuk.com/safe-480x360.jpg)

